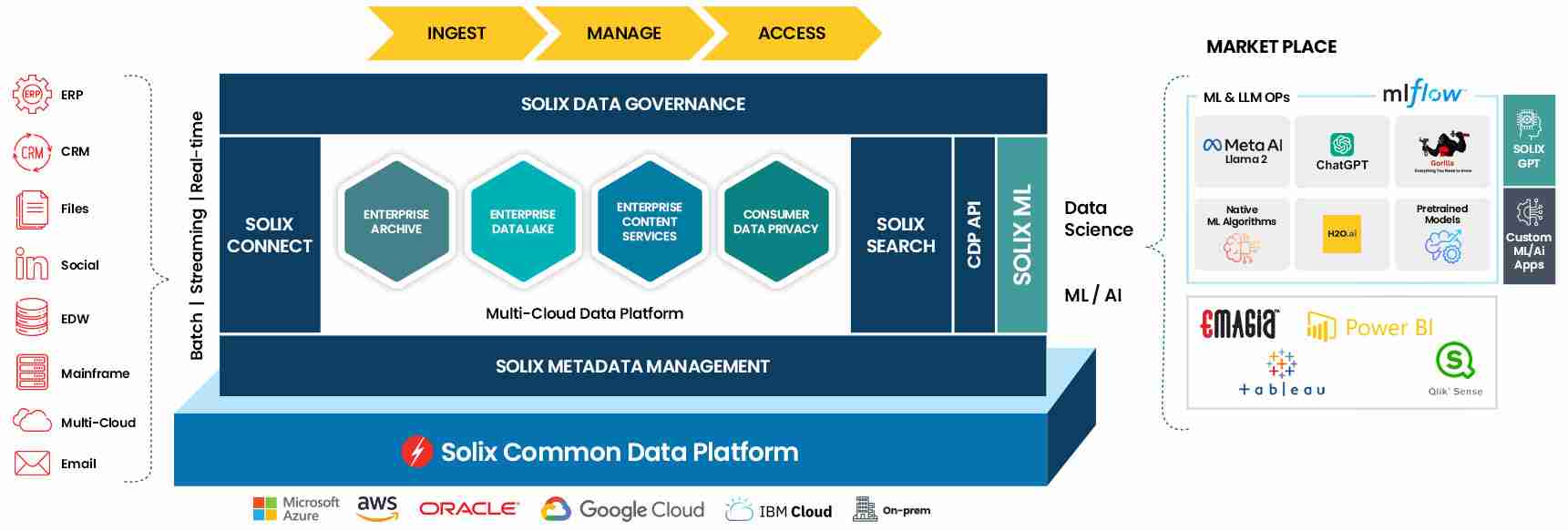
https://www.solix.com/articles..../data-lakes-for-ente
Data Lake Security & Compliance: Enterprise Best Practices
Explore data lake security strategies for enterprises. Learn how Solix ensures compliance, governance, and protection in modern cloud data lake systems.



samdiago123
https://www.solix.com/products..../answers/essential-g
How to Describe a Table in SQL Server: Essential Guide for Developers
Learn how to describe SQL Server table structure—columns, types, constraints—using SP_HELP or system views. Simplify with Solix DataLake.
https://www.solix.com/kb/tpc-ds/
TPC-DS Benchmark Explained: Measuring Data Warehouse Performance
Discover TPC-DS—the industry-standard decision support benchmark—for measuring query speed, throughput, and data maintenance in data warehouse systems.
https://www.solix.com/products..../application-retirem
Solix Application Retirement | Decommission Legacy Applications Securely
Reduce infrastructure costs and retain access to legacy application data using Solix Application Retirement. Securely archive, search, and manage decommissioned data with policy-based retention, legal holds, and role-based access.
"Solix application retirement
legacy application decommission
cloud archive legacy apps
application retirement governance"
Data Encryption Techniques for Enterprise Info Protection | Solix
Discover essential data encryption methods—symmetric, asymmetric, hashing, tokenization—for securing enterprise information across all data states. Learn how Solix powers modern encryption strategies.